Introduction – What is Shadow Workplace AI in Australia?
Table of Contents
- Introduction – What is Shadow Workplace AI in Australia?
- How common is Shadow AI and why it matters for Australian businesses
- Australian legal and regulatory risks of Shadow Workplace AI
- Business impact, detection and people risks
- Technical controls for Shadow AI – CASB, zero trust, DLP, UEBA and watermarking
- Practical steps to manage Shadow Workplace AI in Australia
- Conclusion – Turn Shadow AI into a safe advantage

Shadow Workplace AI in Australia is already here, whether leadership has a plan for it or not. Staff copy text into public chatbots, upload customer data to free tools, and test new AI browser extensions on live projects.
Shadow AI means employees using AI systems for work without formal approval, guardrails, or oversight. It is the AI version of “shadow IT” – unsanctioned, hard to see, and risky when it touches sensitive data, regulated industries, or key business decisions as multiple industry analyses now underline.
How common is Shadow AI and why it matters for Australian businesses
Let us start with scale. While there is limited Australia-only data, multiple Australian and global studies show a clear pattern – most employees use unsanctioned apps, including AI tools, to get work done. across sectors and geographies. People want to move faster, so they reach for whatever tool is one Google search away.
For Australian companies, the scary part is not the number of tools, but the value of what flows through them. Recent IBM Cost of a Data Breach reports put the average cost of a data breach in Australia at over AUD 4 million per incident, with the 2024 report citing around AUD 4.26 million. That figure is not AI-specific, but it benchmarks what is at stake when staff paste customer records, internal pricing models, or source code into a public AI service.
There are no reported fines in Australia that name “Shadow AI” as the root cause. But if you strip away the label, many of the underlying behaviours are the same as past incidents – data leaving controlled systems, unclear vendors, weak access controls, and poor logging. Regulators and customers do not really care if the leak came from a spreadsheet or an AI chatbot; they only see that their data was mishandled and that accountability is often murky.
Shadow AI touches every department, from marketing using image generators, to HR testing résumé screening tools, to finance teams running forecasts through online AI models. Without an intentional approach, you end up with multiplying risk and no clear view of where your critical data is going – which is exactly where a structured AI services strategy becomes less a luxury and more a baseline requirement.
https://www.ibm.com/reports/data-breach
Australian legal and regulatory risks of Shadow Workplace AI
Australia does not yet have a neat legal definition of “Shadow AI”. Still, existing laws already apply to what your people do with AI, even if the tool is free, experimental, or used after hours on a personal device – a point echoed in emerging AI security guidance.
The starting point is the Privacy Act 1988 and the Australian Privacy Principles (APPs). When staff send personal or sensitive information to external AI services, you may breach APP 3 (what you collect), APP 6 (how you use and share data), APP 8 (overseas disclosure), and APP 11 (security). For example, a support agent who pastes a full complaint email into a public chatbot might trigger an unauthorised disclosure if that data is stored offshore without proper safeguards. However, some experts argue that engaging with external AI services does not automatically equate to a privacy breach, provided organisations put the right controls in place. With robust data minimisation (e.g. redacting identifiers before sending prompts), clear contractual safeguards around data use and storage, and careful vendor due diligence, it is possible to leverage AI while still complying with APP 3, 6, 8 and 11. From this perspective, the real risk lies less in the technology itself and more in weak governance: unclear policies, ad hoc experimentation by staff, and poor documentation of how personal information flows through AI tools. Rather than banning external AI outright, these commentators recommend a structured approach – approved tools, standard prompt guidelines, privacy impact assessments, and ongoing audits – so teams can tap into AI’s benefits without stepping outside the boundaries of the Privacy Act.
The Notifiable Data Breaches (NDB) scheme also comes into play. If your use of Shadow AI results in unauthorised access to, loss of, or disclosure of personal information that is likely to cause serious harm, and your organisation is covered by the Privacy Act 1988, you must assess the incident and, where it meets the criteria of an eligible data breach, notify the Office of the Australian Information Commissioner (OAIC) and affected individuals. It does not matter that the event started with an “experiment” in a browser tab; the legal effect is the same.
High-risk sectors feel extra pressure. Finance must align with APRA standards around data security and outsourcing, while health organisations face strict health records and confidentiality rules. On top of that, employment and anti-discrimination law can bite when AI-influenced decisions about hiring, promotion, or discipline are biased or cannot be explained. Think of an HR manager quietly using an AI résumé screener that tends to rank certain age groups lower; that can later become evidence in a Fair Work or discrimination claim.
While there are no public enforcement cases that explicitly blame Shadow AI yet, the maximum penalties for serious or repeated privacy breaches in Australia now reach the greater of AUD$50 million, three times the value of any benefit obtained from the misuse of information, or 30% of a company’s adjusted turnover during the relevant period. This makes Shadow AI less of a future worry and more of a current compliance gap that boards and executives in Australia need to close – often with help from specialist AI partners who understand local regulation.
https://www.oaic.gov.au/privacy/privacy-act/the-privacy-act
Business impact, detection and people risks
Legal risk is only part of the story. Shadow Workplace AI also creates broad business impact that shows up in budgets, reputation, and how teams work with each other when there is no coherent enterprise AI plan.
On the privacy front, fines under the Privacy Act can reach up to AUD 2.5 million for individuals, and for organisations can climb as high as AUD 50 million – or even more, depending on the benefit obtained or a percentage of turnover – after recent reforms. Major non-AI cases such as Optus and Medibank have become benchmarks in boardrooms for how bad a breach can get, even though AI was not the direct cause. When leaders hear those numbers, they start asking sharper questions about any uncontrolled data flows, including AI tools used under the radar.
Sector-specific risk is uneven. Finance and healthcare operate under tougher regulatory expectations and deal with more sensitive data, so Shadow AI incidents there tend to have greater consequences. A stray dataset in a marketing team is bad enough, but an unapproved AI tool handling patient histories or transaction logs carries a very different level of concern. Small and medium enterprises (SMEs) are often hit hardest, because they have less mature governance, fewer internal experts, and limited capacity to absorb a major incident – which makes using professional Australian AI services a pragmatic safety net.
Stakeholders also feel distinct effects. Boards face reputational damage and investor pressure if AI-related incidents reveal weak oversight. IT and security teams struggle with visibility gaps, caught between employees experimenting with AI and senior leaders demanding innovation. HR and legal teams must unpack complex issues around bias, due process, and explainability when AI touches staff or customer decisions. Individual workers are not immune; many employment contracts already prohibit sharing confidential information with unauthorised tools, even if that clause does not mention AI.
Detecting Shadow Workplace AI is tricky because AI often hides inside other tools. Many SaaS platforms now ship with AI assistants turned on by default, so you are not just looking for obvious chatbot websites, but invisible AI features threaded through your existing stack and buried in everyday workflows.
Network traffic analysis and SaaS management tools can spot outbound API calls to major AI providers, such as OpenAI or Google, even when staff try new tools without telling IT. Security teams can then map which business units are driving that traffic and which use cases look risky, such as uploads of large files at strange hours.
Data loss prevention (DLP) tools and endpoint scanners can be tuned for AI-specific patterns, such as prompts that include personally identifiable information, customer numbers, health details, or code files. Browser extension audits matter because many AI helpers live in extensions that quietly read page content or form fields.
SaaS usage analytics can surface AI features being used inside approved platforms, like meeting tools that auto-summarise calls with third-party AI engines. Pairing this with short staff surveys and interviews often reveals creative use cases that tools alone would miss. People will usually talk about what works for them if they trust that you are not just there to shut things down – especially when you can point them towards secure, sanctioned AI alternatives.
User and entity behaviour analytics (UEBA) can flag suspicious patterns that might link to AI automation, such as one account suddenly accessing large volumes of data, or unusual export behaviour. Hands-on checks of API keys, scripts, and automation workflows help security teams confirm whether AI services sit behind those patterns. Even though local prevalence data is limited, global evidence strongly suggests that Shadow AI is common, especially among SMEs trying to do more with less.
https://cloud.google.com/blog/products/identity-security/how-to-detect-shadow-it
Technical controls for Shadow AI – CASB, zero trust, DLP, UEBA and watermarking
Once you can see Shadow AI, the next step is gaining control without killing innovation. This is where specific security technologies become central, especially for mid-sized and larger Australian organisations wrestling with hidden AI usage.
Cloud access security brokers (CASB) act as a smart gatekeeper for cloud traffic. They give you visibility over which AI sites and APIs staff are using and let you block, allow, or conditionally approve them. For instance, you might allow access to a selected AI provider but only from corporate devices, or only for users in certain roles. CASB tools also help you enforce policies consistently across different offices and remote workers.
Zero trust architectures complement this by shifting from perimeter-based thinking to identity and context. Instead of assuming that any device on the network is safe, zero trust models demand strong authentication, fine-grained access controls, and continuous checks. That reduces the chance that a compromised device or account can quietly push sensitive data into AI tools without detection.
DLP and UEBA fill in important gaps. With tuned DLP rules, you can detect prompts that contain personal data, client names, or other sensitive content, and either block them or alert a monitoring team. UEBA, meanwhile, watches behaviour patterns rather than single events, so it is better at catching slow, automated exfiltration through AI scripts or bots.
Watermarking of AI-generated content is another growing control. When you tag outputs from approved AI tools, you can later trace where that content was used, edited, or shared. This supports quality checks, copyright management, and accountability when teams mix AI and human work. It also opens the door to smart internal policies, such as requiring AI-generated copy to be reviewed by a human before it goes to clients – a pattern you can codify when you deploy governed, custom AI models.
https://www.microsoft.com/en-us/security/blog/2023/04/13/how-to-manage-shadow-ai-risks/
Practical steps to manage Shadow Workplace AI in Australia
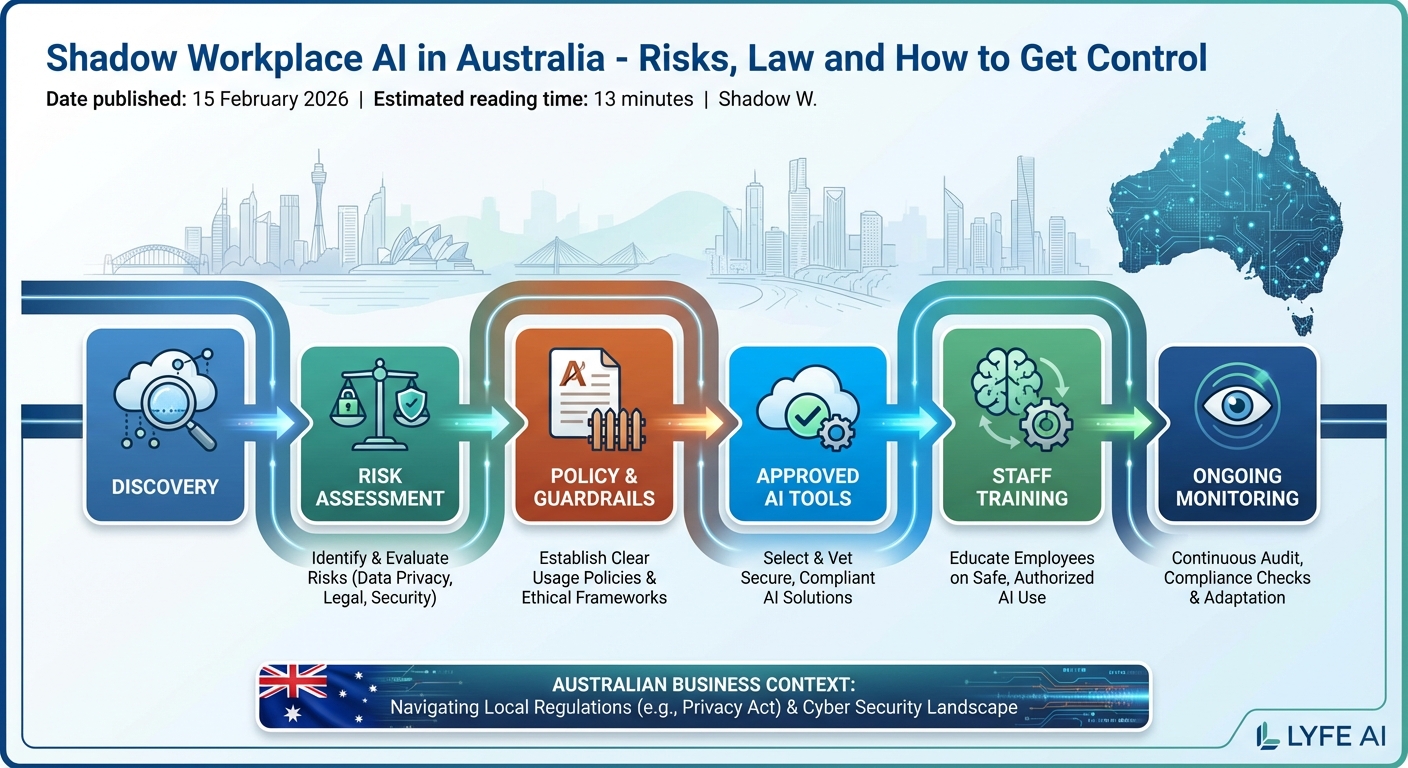
Bringing Shadow Workplace AI under control in Australia is not about banning tools. It is about moving from random, risky experiments to safe, supported use that lines up with your risk appetite and local regulation – often via a mix of internal governance and specialised AI advisory services.
A practical road map often looks like this:
- Baseline your current state. Use network and SaaS discovery to map existing AI usage and run short staff surveys asking how and where people already use AI at work.
- Set clear guardrails. Write plain-language AI use guidelines that cover what data can never go into external tools, what tools are allowed, and how staff should seek approval for new use cases.
- Choose approved tools. Select a small set of sanctioned AI services with strong privacy, security, and data residency controls. Provide access so people do not feel forced to sneak around policies, for example by rolling out a secure Australian AI assistant that staff can actually rely on.
- Strengthen security controls. Tune DLP for AI prompts, deploy or configure CASB where possible, and review access rights in line with zero trust principles.
- Educate and repeat. Run regular training for staff and managers focused on real examples of Shadow AI risk in Australian contexts, not abstract threats.
Treat this as an ongoing program, not a one-off project. AI tools will keep changing, and so will the ways your teams use them. Regular reviews, incident simulations, and updates to your AI policy help you stay ahead of new opportunities and new risks – a cycle that is easier when your AI stack and policies are documented, from model choices like GPT 5.2 variants and OpenAI mini models through to broader options such as Gemini 3 Pro comparisons.
Conclusion – Turn Shadow AI into a safe advantage
Shadow Workplace AI in Australia will not vanish. Your people reach for AI because they want to move faster and do better work. The task for leaders is to turn that raw energy into something safe, compliant, and aligned with your strategy, rather than a web of hidden AI practices waiting to surface at the worst possible moment.
By understanding the scale of Shadow AI, the legal and sector-specific risks, and the technical controls available, you can move from guesswork to structured action. Map your current use, set clear rules, choose trusted tools, and keep your security posture evolving as AI evolves – and make sure your own policies, such as AI-related terms and conditions, keep pace.
If you are ready to bring Shadow AI out of the dark and build a confident, compliant AI program, now is the time to act – engage your security, legal, and business teams, and start designing the guardrails that will let AI become a real advantage rather than a hidden liability, ideally anchored in a documented AI landscape that is as transparent as your own governed AI content and workflows.
Frequently Asked Questions
What is shadow AI in the workplace and how is it different from normal AI use?
Shadow AI in the workplace means employees are using AI tools for work without formal approval, policies, or oversight from the organisation. Unlike sanctioned AI, which is vetted, procured and monitored by IT, privacy, and legal teams, shadow AI typically involves free or consumer tools, browser extensions, or personal accounts that sit completely outside company controls.
Why is shadow workplace AI such a big risk for Australian businesses?
Shadow AI is risky because staff can paste customer records, financial data, source code, or confidential documents into public AI tools with little understanding of where that data goes. For Australian organisations, this can trigger privacy breaches under the Privacy Act, increase the chance of cyber incidents, and create compliance gaps with contracts, sector regulations, and internal policies.
Is using ChatGPT or other public AI tools at work legal in Australia?
Using tools like ChatGPT at work is not automatically illegal in Australia, but how you use them can create legal problems. If employees upload personal information, confidential client data, or regulated content without consent or safeguards, this can breach the Privacy Act, confidentiality obligations, NDAs, industry codes, or internal information security policies.
What Australian laws apply to shadow AI and unsanctioned AI tools at work?
The key legal frameworks are the Privacy Act 1988 (Cth), which governs handling of personal information, and the Australian Privacy Principles (APPs), especially around overseas disclosure and security of personal data. Depending on the sector, organisations may also need to consider the Corporations Act, APRA CPS 234, critical infrastructure rules, cyber‑security obligations, contract and IP laws, and any workplace surveillance or monitoring requirements in their state or territory.
How can I tell if our staff are using shadow AI tools in my organisation?
Detection usually involves combining technical monitoring with staff engagement. Australian organisations commonly review network and DNS logs, SaaS usage reports, browser extension inventories, and data loss prevention alerts, while also running anonymous staff surveys, interviews, and workshops to surface which AI tools people actually use and why.
What steps should Australian companies take to bring shadow workplace AI under control?
Start by mapping current AI use (including shadow tools), then define clear policies that say what data can and cannot go into AI systems. Next, provide safe, approved AI options, roll out training for staff and managers, update contracts and vendor due‑diligence for AI providers, and implement monitoring and incident response processes specifically for AI‑related data leaks or misuse.
How can LYFE AI help my business manage shadow AI risk in Australia?
LYFE AI helps organisations identify where shadow AI is already being used, assess the related legal, privacy and cyber risks, and design practical controls. They can support you to create an AI use policy, select and configure safe AI tools, build governance frameworks, train staff and leaders, and establish ongoing monitoring so AI remains compliant and aligned with Australian law and your risk appetite.
What is the best way to create an AI policy for employees in an Australian company?
A good AI policy clearly explains allowed and prohibited use cases, what types of data must never be put into public AI tools, and which approved AI platforms staff should use instead. It should reference relevant Australian privacy and security obligations, set out approval workflows for new AI tools, and be paired with training, examples, and accessible guidance rather than just a static PDF on the intranet.
Can shadow AI use lead to data breaches and privacy notifications in Australia?
Yes, if employees feed personal or sensitive information into unsanctioned AI tools and that data is exposed or mishandled, it can amount to an eligible data breach under the Notifiable Data Breaches scheme. In that case, the organisation may need to notify the OAIC and affected individuals, and could face investigation, reputational damage, and remediation costs even if the incident started with a single AI query.
How do sanctioned enterprise AI tools compare to free public AI for Australian businesses?
Enterprise AI tools usually offer clearer data handling terms, options to keep prompts and outputs out of model training, stronger security controls, and better logging and admin controls to support Australian privacy and compliance obligations. Free public AI tools are faster to adopt but provide limited control or visibility, making it much harder to prove compliance or investigate incidents if something goes wrong.


